Policy and Basic Mindset
UBE Group Information Management Guidelines
We protect information and properly disclose our corporate information.
- We strive to protect personal information and the information of our business partners.
- We use every precaution for the handling of undisclosed corporate information (insider information) and the Group’s confidential information.
- We promptly and fairly disclose and supply accurate corporate information to stakeholders.
UBE Group Basic Policy for Information Security
The UBE Group will build a robust information security system and permanently prevent cyber security damage, thereby enhancing corporate credibility, developing relationships with stakeholders, and enhancing corporate value. In addition, the Group aims to earn the trust and recognition of society by appropriately disclosing, utilizing, and protecting data as well as appropriately managing the data assets of companies.
Scope
This policy applies to the UBE Group (UBE Corporation and its consolidated subsidiaries). It also applies to group companies that are not included in the scope of consolidation but share the network.
Goal
With a high level of security literacy among all employees and a robust information security system through the introduction of advanced security measures, we aim to be a leading security-oriented corporate group that can withstand various cyberattacks. To achieve this, we will implement the following measures.
- We will strengthen education and training to further improve security awareness among all employees.
- We will strengthen physical security measures at all business sites to prevent unauthorized intrusion.
- We will strengthen our technical security measures in response to evolving cyber threats and increase our cyberattack resilience.
Commitment
- Maintain zero security incidents with external impact per year.
- Maintain a 100% participation rate in information security education
- By the end of FY2027, an information security assessment score of 900 by Secure SketCH
- By 2027, 100% compliance rate with regulations and standards in each workplace
- By 2027, targeted attack e-mail training: 5% or less open rate, 75% or more open notification rate
- By 2027, Vulnerability assessments of all Group companies.
Responsible Departments and Review
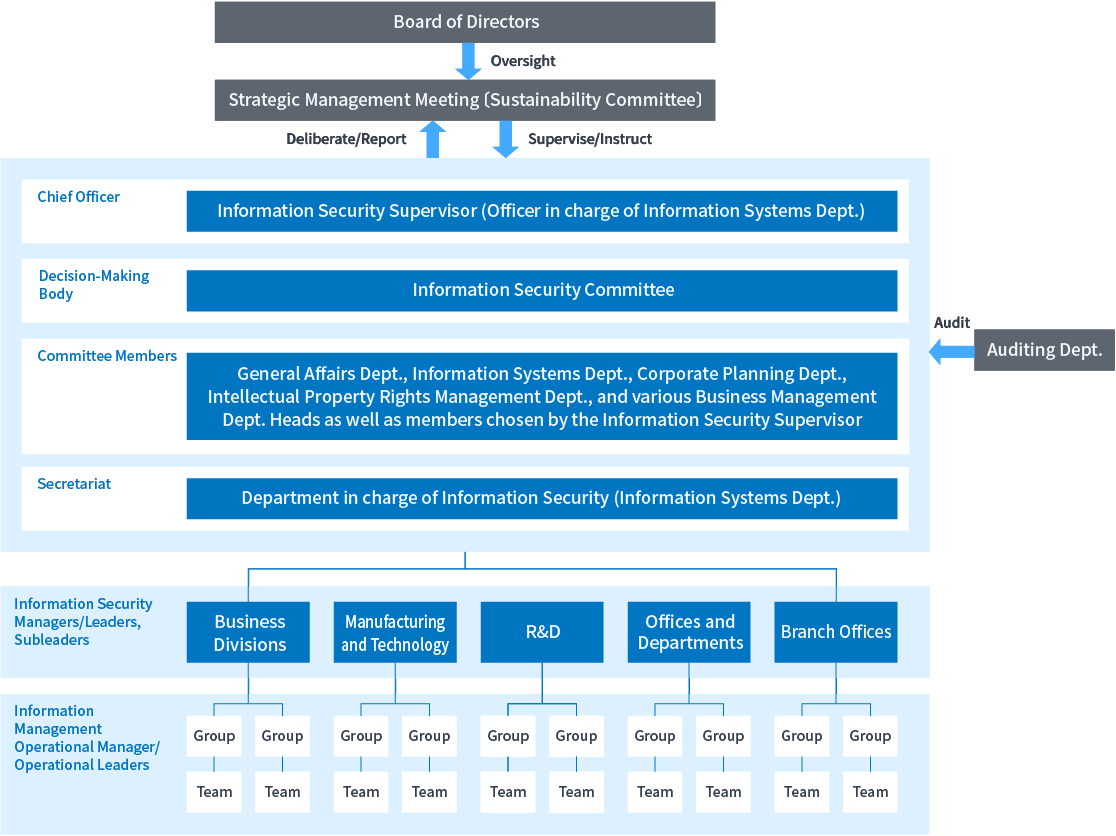
The Information Systems Department is responsible for overseeing and managing this policy.
This Policy is subject to regular review once every three years, in alignment with the Medium-Term Management Plan. Any revisions, whether as part of a scheduled review or required during the period, will be deliberated and approved by the Information Security Committee.
Personal Information Protection (Privacy Policy)
The UBE Group has established the following Privacy Policy, and is taking initiatives to implement, maintain, and improve its measures for personal information protection.
- The UBE Group has established and shall comply with rules concerning the appropriate handling of personal information, taking into consideration the details and scale of the Group’s business. These rules pertain to the acquisition, usage, transfer, safekeeping, provision, and deletion of personal information.
- The UBE Group shall practice regulatory compliance with laws and ordinances concerning personal information protection.
- The UBE Group will carry out safety measures to ensure against incidents such as the loss, destruction, falsification, and leakage of personal information. Furthermore, the Group will act quickly to implement necessary corrective actions should any such incident occur.
- The UBE Group will regularly reassess and improve its policy on personal information protection.